Timeline
Timeline for 2-second unlocking vulnerability
[ May 12, 2016 ]
1) On May 12, 2016, the date of the hack, stardust uploaded a post about the incident on a Korean community website and DAO support page.
[Urgent]Buying DAO using Mist has hacked
Link
https://forum.daohub.org/t/urgent-buying-dao-using-mist-has-hacked/1742
http://www.ddengle.com/bitcoinshare/1228224
2) In the middle of the mayhem of wild assumptions about how Mist had been compromised, someone found that there has been a line of code that unlocks and leaves your Mist wallet unprotected for 2 seconds.
Link
https://github.com/ethereum/mist/blob/master/interface/client/templates/popupWindows/sendTransactionConfirmation.js#L201
“web3.personal.unlockAccount(Session.get('data').from, pw || '', 2, function(e, res){ “
3) cpplover(trustfarm) asked for cooperation on the Ethereum Forum to forestall the hacker's attempts to exchange the stolen Ether with other currencies.
Link
https://forum.ethereum.org/discussion/6818/urgent-7218-eth-hacked-when-using-mist-needs-community-power-and-interesting#latest
The only thing that could be done was to leave a comment on the hacker’s address on ‘etherscan.io’ and ‘etherchain.org’ as “Stolen eth 7218 from Patrick ( 0x95a3bA0AabC6296CbBE3862a889EcB37979dA493 ) plz refer”
[ From May 12 to 14, 2016 ]
4) The victim, Patrick(stardust), after discovering the code that opens Mist wallet for 2 seconds, thoroughly inspected his server's logs and ended up finding some peculiar entries in his UFW, Ubuntu Firewall logs.
Patrick reconnected to the network and began real time packet sniffing, suspecting that the peculiarities in his logs were the result of a bot.
5) It was confirmed that two bots that matched the suspicious logs on UFW were periodically monitoring the node attributes as below.
• eth_accounts - Wallet's address check
• eth_mining - Check if a targeted server is mining
• miner_setEtherBase - Setup a Etherbase
• eth_getBalance - Wallet's balance check
6) After watching bots’ suspicious patterns, Patrick had a hunch that there must be a relationship between the bots and the 2-second unlock code. He then ran Mist and watched what happens when transferring ETH on Mist.
7) As expected, it’s been observed that the bots try to transfer ETH to the hacker’s address (or pre-designated address) using “eth.sendTransaction” when a balance of a targeted wallet changes by a real owner’s transfer.
[ May 14, 2016 ]
8) Patrick gave a demonstration that the hacker’s attack succeeds with the 2-second vulnerability on a Youtube video and is continuously updated with the details on the links below.
Link
https://forum.daohub.org/t/urgent-buying-dao-using-mist-has-hacked/1742
Community members' comments about additional potential attacks and the measures for Mist investigation.
Link
https://forum.daohub.org/t/urgent-buying-dao-using-mist-has-hacked/1742/53
Trustfarm sent Github developers the related information and asked for an explanation for better understanding and countermeasure against the vulnerability .
Link
https://github.com/ethereum/mist/issues/611#issuecomment-218736838
A developer expressed his feelings and said there's nothing that can possibly be done for the case as below.
[ comment ]
9) Another developer acknowledged the problem of the 2-second unlocking vulnerability but avoided a further discussion saying that this is just a user’s fault. Meanwhile, however, on the very same day the Ethereum dev team started working on a new method, “SignAndSendTransaction”.
eth: add new RPC method (personal.) SignAndSendTransaction #2564
Link
https://github.com/ethereum/go-ethereum/pull/2564
The following included text makes it clear that this update is intended to address the 2-second unlocking vulnerability.
This PR introduces a new RPC method PrivateAccountAPI.SignAndSendTransaction that is exposed in the personal namespace. The method accepts a transaction and password as arguments. This allows external applications to submit a transaction without the need to first unlock an account before submitting a transaction which can give an adversary a small time window to submit a fraudulent transaction or sign data.
[ May 16, 2016 ]
10) Patrick succeeded in demonstrating the attack on a general network cat utility and also Ubuntu and Windows using IPC. He then uploaded the detail about IPC attacks to the forum.
Command on Ubuntu:
echo '{"jsonrpc":"2.0","method":"ete150d1d95dd975e458f1ec2a210","value": "100000000000000000"}],"id":1}' | nc -U ~/.ethereum/geth.ipc0388e
If it succeeds,
{"id":1,"jsonrpc":"2.0","result":"0xb6c16f2bd73f64c9a8bc126d917826e2cc637259d7562403804c719a9e89bd03"}
Command on Ubuntu, Windows:
geth --exec "web3.eth.sendTransaction({from:eth.accounts[0], to:eth.accounts[1], value: web3.toWei(0.001, 'ether')})" attach
On executing the codes above consecutively, ether gets hijacked on the moment of “UnlockAccount()” on Mist.
The video of IPC attack demonstration:
11) After, on the additional testing, it was discovered that the user’s password was being recorded in the log unencrypted. This vulnerability was also reported on Dao’s forum. The Ethereum dev team didn’t directly respond to the post but started working on a new patch for password filtering. It seems that the dev team was aware of the severity of the vulnerability but they maintained their attitude and described this issue as a minor problem.
cmd/geth: fix console history exclusion #2567
Link
https://github.com/ethereum/go-ethereum/pull/2567
The execert below mentions a precise exclusion of personal information on console.
Calls to 'personal' API should be excluded from console history because
they can be called with an account passphrase as argument. The check for
such calls was inverted and didn't work.
Regarding this matter, a professional in the security field left the following comment.
"summary
I have a history of auditing financial institutions. If such set of apps as mentioned above would ever had chance to evolve into working product in any bigger corpo first audit, even internal one, will lead to project suspension/cancellation. Of course only somewhere where security matters as no such corpo likes to cover clients loses."
Link
https://forum.daohub.org/t/the-mist-geth-hack-urgently-needs-our-attention-again/3082/29
[ From May 15 to 17, 2016 ]
12) Seunghwan Han from EthereumKorea sent a statement to the people in charge, who are working for Ethereum Foundation and Daohub, to ask for cooperation and warn them of the security holes on behalf of the victim, Patrick, and Korean Ethereum community. There has not been a reply of any kind as of now.(6/2).
[ May 21, 2016 ]
13) Patrick asked for an explanation and one developer replied that the update is done, not for Mist’s security problem, but just for incautious users as a precaution. He still maintained his claim that users are to blame for the hacking.
" And we still maintain that the cause of theft was an improper use of the program, as it was stated everywhere that opening up access to your node to the internet is an extremely bad idea waiting for abuse.
We are not patching the software to plug up any security holes (it works as intended), rather we are extending it feature wise to ensure that someone not careful enough doesn't get bitten again so easily. It's just an extra security precaution to protect the users."
Link
https://github.com/ethereum/go-ethereum/pull/2564
[ May 23, 2016 ]
14) One Korean security specialist mentioned that this is a clear negligence about the security SW guide that states that user’s personal information must be encrypted at every level and there must be a multiple of security measures. Moreover it is irresponsible and immoral for the developers to blame users while they are the ones who should protect the users.
[ May 24, 2016 ]
15) Atomrigs from Korean Ethereum meetup raised concerns about the entire ethereum wallet codebase and proposed some important measures to improve security.
The Mist/Geth Hack Urgently Needs Our Attention Again
Link
https://forum.daohub.org/t/the-mist-geth-hack-urgently-needs-our-attention-again/3082
16) Key individuals in Ethereum accused us of blackmail,but this was never the case. Rather, Patrick and his supporters volunteered to pinpoint the vulnerability and analyze it for a solution. And by doing their best with time, effort, and resources available to them, they succeeded in triggering a series of major updates (done or planned). There was comment about compensation for Patrick’s loss and contribution but this was no other than a reasonable demand to help Patrick’s tragedy as a victim and contributor. There was no intention of blackmailing at all.
17) trustfarm showed a video demonstration on how to make generic malware to help people understand how easy to compromise Mist through both RPC and IPC as well as how severe the vulnerability is. This subject is being discussed on the dao slack channel.
Link
https://forum.daohub.org/t/the-mist-geth-hack-urgently-needs-our-attention-again/3082/14
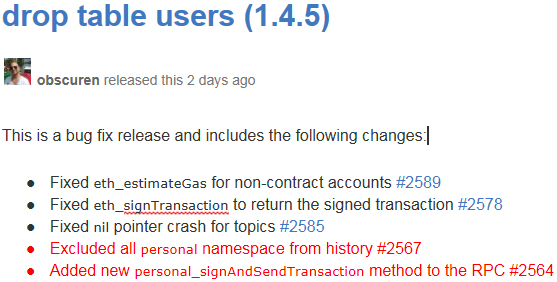
18) Ethereum Dev released Geth1.4.5 with the two issues reported fixed.
It is commendable that regardless of placing the blame on users,, the devs patched the exposed vulnerabilities in a swift manner. This shows that the dev was also aware of the severity of the vulnerabilities. However, it is very unfortunate that there has been no acknowledgement at all for Patrick, who is the largest victim and contributor to exposing the the vulnerabilities.
Link
https://github.com/ethereum/go-ethereum/releases
[ May 26, 2016 ]
19) Stephan Tual from The DAO announced a proposal for DAO Framework security enhancement.
DAO.Security, a Proposal to guarantee the integrity of The DAO
Link
https://blog.slock.it/dao-security-a-proposal-to-guarantee-the-integrity-of-the-dao-3473899ace9d#.krwv1wgv3
In the post, there are some security suggestions that we have already mentioned on the previous post on May 23, 2016. Quoting our suggestions, a fund of 125,000 ETH is being raised to address security issues, which we applaud.
A summary of costs can be found below:
Update of The DAO Framework to Version 1.1, including addressing the current issue list as it stands on Wed 25/05/16, and including advanced testing and code review — 10,000 ETH
Deployment of 2–3 of our best security experts, including DAO Framework Author Christoph Jentzsch at any given time, for the next 2 years, with an ‘on call’ schedule 24/7 — 60,000 ETH
External audits to review the code — 25,000 ETH
Assigned to the bug bounty program — 30,000 ETH
Total- 125,000 ETH
This proposal indicates that there must be serious concerns about security among people in Ethereum Foundation.
[ May 29, 2016 ]
20) Tasks to be done
The vulnerabilities reported have been patched, but there are still some major security related issues being discussed by community members.
- Passwords are still being delivered from Mist to Geth unencrypted. There is a potential risk that the password can be intercepted in the middle of the process.
This was exemplified by the case of an iOS attack for hacking the iPHONE's secure password using IPC
http://www.symantec.com/connect/blogs/apple-vulnerabilities-pose-serious-threat-passwords-and-credentials
Thus, passwords should be encrypted before a transfer from Mist to Geth or there should be a modification to the whole communication method between them to be more secure.
- There needs to be an identity confirmation system for clients when Geth allows other clients, including Mist, to connect to itself. Geth could register, for example, a public key for each client in advance and authorize with it to block unregistered clients' connection attempts.
- There must be a double safety measure for preventing keys stored in Keystorage from being individually copied.
- Finally, it would be very hard to earn the software’s credibility back and take care of the users’ concerns without a systematic security enhancement.
[ May 30, 2016 ]
Patrick and community members who support better security for Ethereum are still looking forward to having an open and constructive discussion with the Ethereum Foundation.
E-mail : admin@security7218.org





